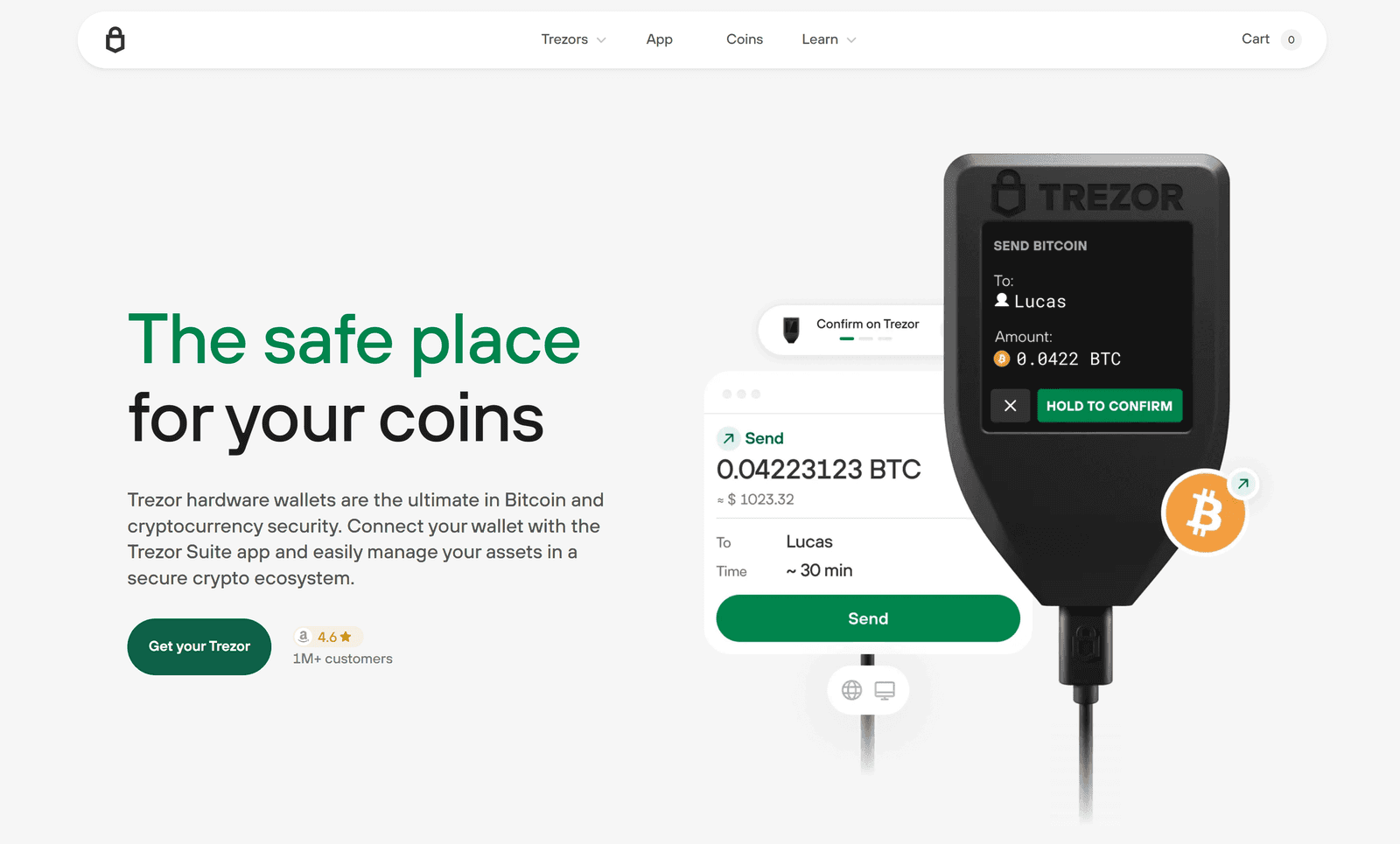
Trezor Suite: A Complete Guide to Secure, Simple, and Powerful Crypto Management
Introduction to Trezor Suite
Trezor Suite is the official software interface designed to work seamlessly with Trezor hardware wallets. It acts as a control center where users can manage, protect, and grow their cryptocurrency holdings with confidence. Built with security, privacy, and usability at its core, Trezor Suite goes far beyond being just a wallet interface—it is a complete crypto management ecosystem.
In a world where digital assets are increasingly targeted by hackers, phishing scams, and malware, Trezor Suite stands out by giving users full control of their private keys while offering a clean and intuitive experience. Whether you are a beginner entering the crypto space or an experienced investor managing multiple assets, Trezor Suite provides the tools you need without sacrificing safety.
What Makes Trezor Suite Different?
A Privacy-First Philosophy
One of the defining features of Trezor Suite is its strong commitment to user privacy. Unlike many online wallets and exchanges, Trezor Suite does not track user activity or collect personal data. Transactions are handled locally, and users can even route traffic through the Tor network for enhanced anonymity.
This privacy-first approach ensures that your financial activity remains your own—free from unnecessary third-party monitoring.
Core Features of Trezor Suite
Secure Asset Management
At its heart, Trezor Suite allows users to store, send, receive, and manage cryptocurrencies securely. Because it is paired with a Trezor hardware wallet, private keys never leave the device. This drastically reduces the risk of theft, even if your computer is compromised.
Multi-Currency Support
Trezor Suite supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, Litecoin, Cardano, and thousands of ERC-20 tokens. This makes it easy to manage a diverse portfolio from a single dashboard without juggling multiple apps or wallets.
Built-In Portfolio Overview
The portfolio dashboard provides a clear overview of your holdings, balances, and transaction history. Users can track performance over time and see asset allocation at a glance, making it easier to make informed decisions.
User Experience and Interface Design
Clean, Intuitive Design
Trezor Suite is designed with simplicity in mind. The interface is modern, minimal, and easy to navigate, even for users who are new to cryptocurrency. Clear labels, guided steps, and helpful warnings reduce the chance of costly mistakes.
Desktop and Web Flexibility
Trezor Suite is available as both a desktop application and a web-based interface. The desktop version offers maximum security, while the web version provides convenience for users who need quick access. This flexibility allows users to choose the setup that best fits their lifestyle and risk tolerance.
Advanced Security Features
Hardware-Level Protection
Because Trezor Suite works with Trezor hardware wallets, all sensitive actions—such as signing transactions—must be physically confirmed on the device. This extra layer of verification protects users from malware and remote attacks.
Passphrase and Backup Options
Users can enhance security by enabling passphrases, creating hidden wallets that are inaccessible without the correct phrase. Trezor Suite also guides users through secure backup processes using recovery seeds, ensuring funds can be restored even if the device is lost or damaged.
Open-Source Transparency
Trezor Suite is open-source software, meaning its code is publicly available for review. This transparency allows the global security community to audit and improve the software, increasing trust and reliability.
Advantages of Using Trezor Suite
Full Control Over Your Assets
One of the biggest advantages of Trezor Suite is true ownership. Users control their private keys at all times, unlike exchange wallets where funds are technically held by a third party.
Reduced Risk of Hacks
By keeping private keys offline and requiring physical confirmation, Trezor Suite dramatically reduces the risk of hacks, phishing attacks, and unauthorized access.
No Dependence on Centralized Exchanges
Trezor Suite allows users to manage assets independently, reducing reliance on centralized platforms that may face outages, freezes, or regulatory issues.
Seamless Integration with Security Best Practices
From firmware updates to transaction verification, Trezor Suite actively encourages secure behavior without overwhelming the user.
Benefits for Different Types of Users
Beginners in Crypto
For newcomers, Trezor Suite offers guided onboarding, clear explanations, and safety checks that help users learn while staying protected. It removes much of the fear associated with managing digital assets.
Long-Term Investors
Long-term holders benefit from Trezor Suite’s cold storage model, portfolio tracking, and peace of mind knowing their assets are secure over time.
Advanced and Privacy-Focused Users
Advanced users appreciate features like Tor integration, coin control, and passphrase-protected wallets. These tools allow for granular control and enhanced privacy.
Continuous Updates and Ecosystem Growth
Regular Improvements
Trezor Suite is actively developed, with frequent updates that introduce new features, improve performance, and respond to emerging security threats. This ensures the software remains relevant in the fast-moving crypto landscape.
Expanding Compatibility
As the cryptocurrency ecosystem evolves, Trezor Suite continues to expand support for new networks, tokens, and integrations, keeping users future-ready.
Potential Limitations to Consider
While Trezor Suite is powerful, it does require a Trezor hardware wallet, which involves an upfront cost. Additionally, users looking for advanced trading features may still need to connect to external services. However, these trade-offs are intentional, prioritizing security and control over speculation and convenience.
Final Thoughts: Why Trezor Suite Is an Amazing Choice
Trezor Suite is more than just wallet software—it is a statement about how cryptocurrency should be managed: securely, privately, and independently. By combining robust hardware security with a polished and user-friendly interface, it bridges the gap between advanced protection and everyday usability.